Table of Contents
From an IT networking perspective, a proxy server is a dedicated application that acts as an intermediary between a client that requests a resource and the server that provides that resource. More specifically, their main purpose is to receive the request coming from that client and process it accordingly with a set of pre-defined rules that might require forwarding it to the server, as well as serving a previously retrieved (and cached) response, denying the connection, and so on.
In this post, we'll briefly list the various types of proxy servers available nowadays.
Why do we need a Proxy?
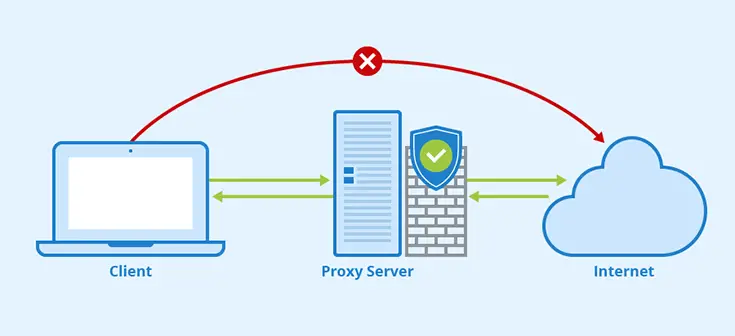
Before starting to enumerate the types of proxy servers available, it might be wise to spend a couple of minutes answering the following question: why do we need a Proxy? Can't we just allow the client to connect and interact with the server without having an "intermediate"? As a matter of fact, the main purpose of a proxy server is to protect the underlying (origin) server from that kind of direct connection/interaction, since it could lead to several performance and security issues.
Here's a list of some good reasons that justify putting a proxy server between our server(s) and their clients.
- Hide the Server IP Address. Every server containing data is a potential target of hackers and malicious third parties: this is the reason why we typically set up firewalls and anti-malware tools. However, most of these external attacks require the attacker to know the IP address of the server. Proxy servers typically have their own dedicated IP address(es) and can be easily set up to prevent tracking of the origin server IP address. To know more about that, check out our edge-origin architecture pattern using NGINX as a reverse proxy.
- Request Filtering. Proxy servers can be easily configured to filter out the requests that don't follow the web server's (or web application's) expected policies, patterns, or endpoints: for example, we can configure them to not serve (deny) a certain kind of file, URL, or HTTP method, regardless of the underlying server or application configuration. These filters, if configured properly, can also be a lifesaver against most request-based threats (such as DDoS attacks).
- Content Caching. Proxy servers can cache the content of any underlying website, serving the cached version of certain pages/requests instead of retrieving their content from the origin server every time: this behavior can dramatically help in increasing the performance of most web applications, as they will have fewer requests to handle. For additional info about content caching, check out our How to cache your website with a NGINX reverse proxy article.
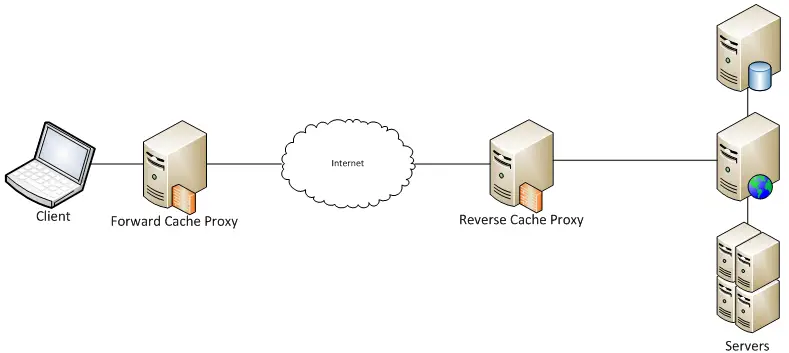
Types of Proxy Servers
Now that we have acknowledged the reasons to have a Proxy, let's see which types of Proxy Servers exist.
SOCKS
SOCKS is one of several protocols used on the internet. Unlike HTTP, this protocol is not designed to tunnel protocols below layer 5. It is designed to handle different kinds of requests, including web browsing, email, and file transfers. The SOCKS proxy server establishes a TCP connection with the actual server, passing packets back and forth. Typically, a SOCKS proxy accepts client connections on TCP port 1080. SOCKS can be a great way to bypass geo-restrictions that are commonly used to restrict access to certain websites and services. These restrictions use your IP address to determine your physical location, and if your location isn't approved, they will block your access. SOCKS5 allows you to circumvent these restrictions by masking your IP address with the server's IP address.
HTTP
This kind of proxy is meant to process a one-way request to the web pages using HTTP protocols: reverse proxies, as well as most intermediate proxies available on the internet, fall into this category since they use the HTTP protocol to perform their job. As we have previously said, HTTP proxies prevent the transmission of potentially harmful content; they reduce the risk of DDoS and buffer overflow attacks, which could compromise our origin web server(s).
It's worth noting that HTTP proxies can be installed as software appliances (such as NGINX, HAProxy, Varnish, SQUID, and so on), but can also be service workers running on top of a managed environment, such as our CORSFlare - a JavaScript Reverse Proxy which is meant to work from a CloudFlare instance.
HTTPS (or SSL/TLS)
HTTPS proxies work just like their HTTP counterpart, with the difference that they can use the Secure Socket Layer (SSL) and/or Transport Layer Security (TLS) protocols to perform end-to-end encryption and decryption between the client and the server, without either of them being able to detect the proxy's presence. In other words, an HTTPS proxy is a proxy that uses the HTTP protocol over SSL/TLS.
HTTPS proxies have become the standard for most websites and online services, as they ensure a much higher degree of privacy and security.
FTP
This type of proxy server acts as a relay for the File Transfer Protocol to allow the administrators to control connections based on source and destination addresses and user authentication. They can also be configured to cache FTP requests' traffic, as well as limit access to certain file transfer commands, such as put and get, based on source or destination addresses and user authentication.
Conclusion
We have reached the end of our Proxy Server overview: we hope that this info will help other Network Administrators to choose the right proxy server to use for their specific needs.