Table of Contents
- A Strong Password Keeps You Safe
- Small Businesses Aren’t Targeted
- Only Certain Industries are Vulnerable
- Software Keeps You Safe
- Threats Originate Outside the Organization
- Cybersecurity is the Responsibility of IT
- Wi-Fi Passwords Keep Channels Secure
- Computer Viruses are Obvious
- Personal Devices Don’t Need to be Secure
- Total Cybersecurity is an Achievable Goal
Businesses are concerned about cybersecurity now more than ever, and for good reason – it is very difficult to keep track of cyber threats and secure a business against each one. When there are these many sources for potential risk to a business, it is inevitable that rumors and misconceptions spread. Trying to defend against all these without confirming their validity is a waste of time, money, and human resources, which would be better spent fighting credible threats. Blindly believing these cybersecurity myths could even open a business up to legitimate cyber attacks.
In this post we'll do our best to enumerate - and dismantle - the most common myths and false beliefs regarding online security and cyber threats. Before even starting our journey, it could be wise to remember this outstanding quote of John T. Chambers, former executive chairman and CEO of Cisco Systems:
There are two types of companies: those that have been hacked, and those who don't know they have been hacked.
A Strong Password Keeps You Safe
An incredibly common myth that both business and individuals fall for is that all they need to keep safe is a strong password. This is absolutely false. It is a much better policy to enable two-factor authentication wherever possible. Another essential step is to monitor data accessibility within the business. It is common for sensitive information to be accessible to employees who may not have the necessary clearance, and this can leave the company at extreme risk of data theft.
Small Businesses Aren’t Targeted
Many small businesses believe they are at lower risk of cyber attacks because they think a bigger business makes a better target for hackers. This is not true. Hackers sometimes focus on small businesses precisely because they are small and may not have extensive software and security teams to protect their data. A common method of cyber attack is the “spray-and-pray” method, in which hackers use automated systems to randomly target businesses, regardless of their size. Small businesses are easier to attack for these programs too, as many of them do not have the ironclad protections that most big businesses do.
Only Certain Industries are Vulnerable
A variation of the small business myth is the industry myth. This refers to the belief that hackers target one industry over another, and so if a business is in a certain industry, it has a lower risk of being attacked. They may think their data is not worth stealing. However, hackers value any sort of sensitive data. This even includes credit card numbers, phone numbers, and addresses of individuals, which by this logic should be extremely worthless to them. Even if the data they gather from businesses has no resale value, they can still effectively hold it “hostage” and demand a ransom from the business, which leads to them profiting.
Software Keeps You Safe
Most anti-virus softwares try to make consumers believe that using them will make their organizations safe. While this is certainly true to some extent, software cannot and will not protect a business from all threats. Cyber threats are always changing and evolving, and the software cannot anticipate a new kind of threat and safeguard against it in advance. In fact, many data breaches happen because of human factors like negligence, accidental sharing of information, and malicious theft. Software cannot protect a business against its own employees beyond a certain extent. To truly try and secure a business, it is important to provide employee training, insider threat detection, and disaster protection.
Threats Originate Outside the Organization
Much of the discussion around cybersecurity threats centers around external threats, and businesses tend to monitor these extensively. However, internal threats are actually a much bigger risk when it comes to data breaches. There are many factors that can lead to data breaches from employees, including anger at the business or just plain ignorance of cybersecurity policies and procedures. While it is important for businesses to monitor the external environment for threats, it is just as important, if not more, for them to be on the lookout for internal threats and take measures to minimize these.
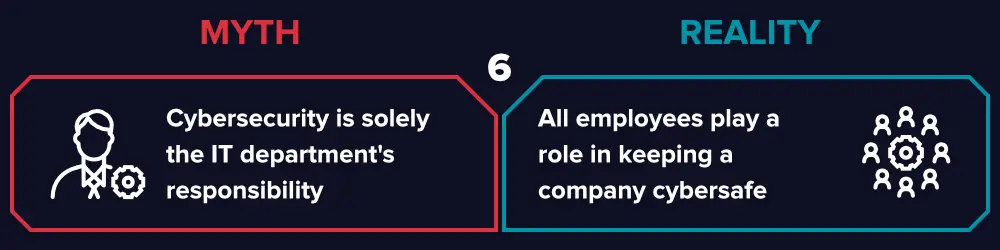
Cybersecurity is the Responsibility of IT
When a breach does happen, people are quick to point fingers to the IT department. The following image should be enough to understand how that's simply not true:
While it is true that IT handles a lot of cybersecurity measures, it is essential to realize that all the employees are actually responsible for the safety of the business. There is no true cybersecurity without the training and awareness of every single employee within a business. Even the simple things, like knowing how to spot a phishing scam and avoiding risky links, can go a long way towards protecting a business from cyber threats.
When a breach does happen, people are quick to point fingers to the IT department. While it is true that IT handles a lot of cybersecurity measures, it is essential to realize that all the employees are actually responsible for the safety of the business. There is no true cybersecurity without the training and awareness of every single employee within a business. Even the simple things, like knowing how to spot a phishing scam and avoiding risky links, can go a long way towards protecting a business from cyber threats.
Wi-Fi Passwords Keep Channels Secure
Many businesses now have employees that work remotely or travel very frequently. Thus, a lot of their work is done on WiFi networks that do not necessarily have the same protections that a business’ network might. In many cases, people assume that a password is enough to keep their data secure even from others accessing the same network. The truth is, people using the same password on the same network can potentially access data that is being transmitted from an employee’s device. Employees should use protective measures such as VPNs to ensure that their sensitive data is secure.
Computer Viruses are Obvious
The media has perpetuated the trope that data breaches or hacks are immediately obvious. While this is effective as a storytelling element and was certainly true ten or so years ago, modern malware does not work like this. It is much more stealthy and difficult to detect. The obvious logic to making a virus that is hard to detect is that it has the time to do a decent amount of damage before anybody even notices it. This is another reason why employee cybersecurity training is so important – they should be able to detect threats and report them before it is too late.
Personal Devices Don’t Need to be Secure
More and more businesses are encouraging Bring Your Own Device (BYOD) policies among employees. While this may be convenient and save costs for the business, it also increases the risk of cyber attacks and data breaches. These personal devices need to have the same protocols and security measures installed as the business’ devices. These rules should cover all devices that can access the internet, including wearable technology and any devices that are a part of the Internet of Things.
Total Cybersecurity is an Achievable Goal
All this said, complete watertight cybersecurity is not a goal that can be achieved and forgotten about. Remember the John T. Chambers statement mentioned at the start of this post: there is no such thing as "total cybersecurity". New threats are always emerging, and every business and individual should do as much as they can to keep their data secure. They must regularly monitor systems, conduct audits, and update and test contingency plans.
The assumption that a business or an individual is incapable of being hacked is dangerously false and should not be considered. It is a must for every employee to be involved with cybersecurity efforts and always keep it in mind when dealing with work-related matters. Cybersecurity is an ideal that requires constant efforts and should always be one of the top priorities for any business.
This post has been originally published here.