A couple days ago I published a post regarding how to protect CentOS server from unwanted SSH login attempts by changing the default port and/or using File2ban. Today I will talk about a very similar issue that affects Windows Server, which is often only accessible from the administrator by using a Remote Desktop (RDP) connection: that's a very common case for any VPS or dedicated server hosted through an ISP.
The issue is the same of CentOS: your system is receiving an insane amount of (failed) login attempts in terms of thousands per day by random attackers who are trying to get in using standard brute-force techniques. Depending on given scenario they can be bots, zombies or hackers running BFA scripts. Luckily enough, there are some rather trivial countermeasures that can be adopted to shielding your system even if you can't afford to purchase and install a Firewall with Intrusion-Prevention System (IPS) - which is something you should really do anyway, expecially if you're hosting some valuable and/or sensitive data. The methods below will work on any Windows Server release: Windows Server 2003, Windows Server 2008, Windows Server 2012, Windows Server 2012 R2 and the new Windows Server 2016.
Restrict RDP access using Windows Firewall
If you didn't do that already, this is the first thing you need to do: there's no reason to make your RDP connection available to the whole internet, as long as you're connecting from the same IP address (or from your local provider's IP address range).
To do that, just open the Windows Control Panel, locate your Windows Firewall, go to its Advanced Settings and find these rules:
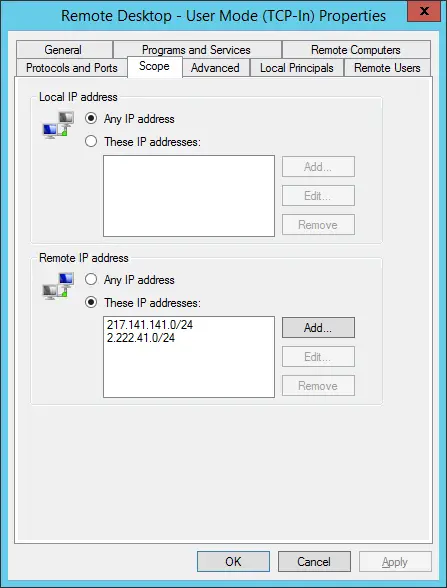
- Remote Desktop - User Mode (TCP-in)
- Remote Desktop - User Mode (UDP-in)
Both of these rules allow access from port 3389, which is the default RDP port. Navigate to the Scope tab and add your IP address(es) to the Remote IP Address list.
Here's an example:
The GUI also gives you the chance to specify an IP address range (Add > This IP address range > From: / To:) or a predefined set of computers from known sources: Default Gateway, DNS Servers, DHCP servers, Local subnet, Internet, Intranet and so on.
This is by far the best thing you can do to protect your server against these attacks.
Change RDP default port
However, there are situations where you just can't do this: for example, if you want to be able to access your server from RDP from a lot of different places, including those you wouldn't be able to allow within this firewall rule's scope as you have no way to know their IP address(es) in advance. If you have this need, the best thing you can do is (at least) to change the RDP default port.
Here's how you can change the listening port of the Remote Desktop service (as explained in this MS official guide).
- Start Registry Editor.
- Locate and then click the following registry subkey:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp\PortNumber
- On the Edit menu, click Modify, and then click Decimal.
- Type the new port number, and then click OK.
- Quit Registry Editor.
- Update your Windows Firewall's Remote Desktop rules accordingly (see above) to avoid being locked out. Alternatively, you can also create two new TCP and UDP rules for the new port and then (optionally) deactivate the default ones: doing that is highly advisable, expecially if you plan to switch back to the default port in the future.
- Restart the RDP service (see below) or just reboot the machine.
Restart the RDP service
To restart the RDP service, just go to the Control Panel > Administrative Tasks > Services (or type services.msc from the Run... prompt or from the command prompt) and restart the Remote Desktop Services:
That's it for now: we sincerely hope that this small guide will help you to shield your server again these kind of attacks.