In this second post dedicated to System Administrators who have to deal with a Risk Assessment, Security Assessment, Due Diligence or Compliance Questionnaire: if you lost the first one, you can read it here. This time we'll talk about how to enforce a password policy by altering the default settings - in terms of password complexity and password minimum length - in Windows Server 2012.
This is a task that often needs to be done to comply with the security requirements asked by most modern regulations and standards - such as the ISO/IEC 27001:2013, ISO/IEC 27002:2013, ISO/IEC 20000:2011, NIST CyberSecurity Framework, SSAE/SOC2, ITIL, PCI-DSS and so on - but it can also be useful for those who just want to protect their system in a better way - or do the exact opposite by relaxing these controls (which is not something you should normally do - read here to understand why).
Here's how we can take a look at the current system settings in terms of password strength and change them as we please:
Networks without Active Directory
In case you need to configure clients and/or servers not connected to an Active Directory Domain, use the following:
- Open the Control Panel.
- Navigate to Administrative Tools > Local Security Policy.
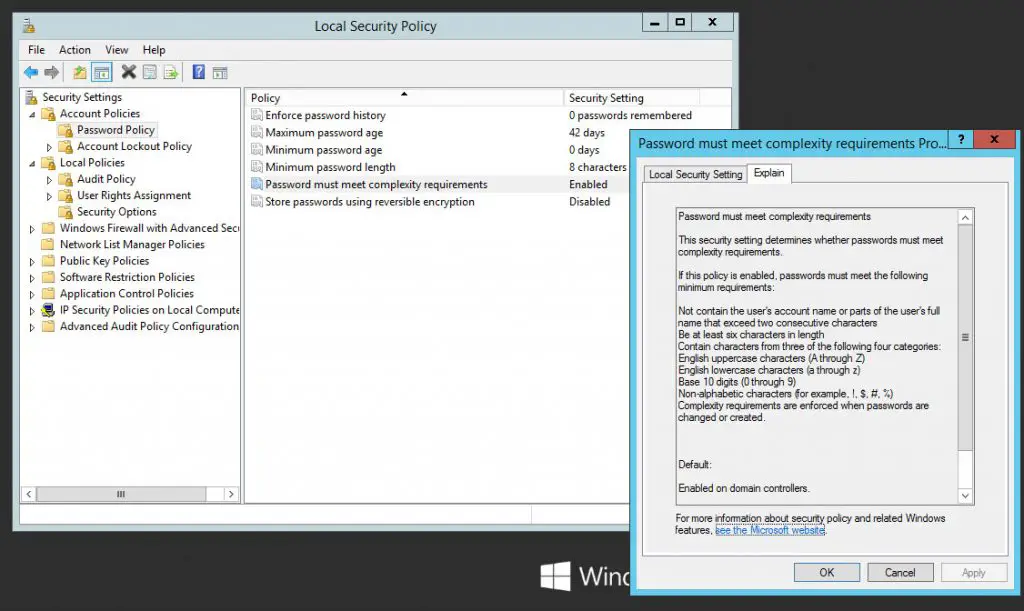
- In the modal window that will open, expand the Security Settings > Account Policies > Password Policy node.
From there, you can view and/or edit the various options available in Windows Server 2012. For example, you can choose to enable or disable the password complexity requirements, which means the following:
If this policy is enabled, passwords must meet the following minimum requirements:
- Not contain the user's account name or parts of the user's full name that exceed two consecutive characters
- Be at least six characters in length
- Contain characters from three of the following four categories:
- English uppercase characters (A through Z)
- English lowercase characters (a through z)
- Base 10 digits (0 through 9)
- Non-alphabetic characters (for example, !, $, #, %)
- Complexity requirements are enforced when passwords are changed or created.
This standard complexity profile can be toggled altering the Password must meet complexity requirements policy.
These are quite good settings, except for the minimum password length: six characters would've been arguably viable for 2012, but are definitely not enough in 2017. Luckily enough, you can override that single option by altering the Minimum password length policy, which should be put to (at least) 8 to fend off most brute-force attacks.
Networks with Active Directory
If your client or server is part of an Active Directory domain, you won't be able to use the Local Security Policy console: if that's the case, use the Group Policy Management console from Control Panel > Administrative Settings of your AD domain controller and edit the GPO settings there.
Conclusion
That's it: we hope that these hints will help other System Administrator to make their system compliant with the latest security standards.
If you're looking for a way to set a idle timeout for Remote Desktop sessions, read this other post.